Ron Mattino
This channel is dedicated to electronics, programming and engineering.

How does the Touchscreen Work? #electronics #diy #engineering #arduino #arduinoproject

Why does an LED need a RESISTOR? The Simplest Explanation.

USB over UTP cable: Testing Voltage Drop and Transfer Speed.

10 Common MYTHS about ELECTRONICS.

Electronics for BEGINNERS: Switch, Relay, Resistor, Diode, Capacitor, Transformer, Transistor, SCR

USB connection over an ETHERNET cable? Making your own 7 meters long USB extender cable from scrap.

Can you build a USB wall charger from scrap? Let's do it!

Do you know how to FAST CHARGE your phone? Fast charging and how it works.

7 Simple Arduino Projects for Beginners
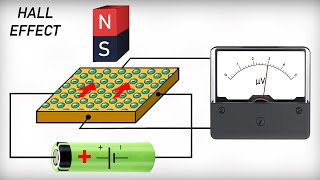
How does the Hall Effect Sensor work? Building a Levitron using the Hall Effect Sensor.

Arduino for BEGINNERS! Set up the BOARD and Write your VERY first sketch in 5 minutes!

How does USB work?

How does NE555 work? Bistable, Monostable, Astable, with schematic examples. The COMPLETE Guide.
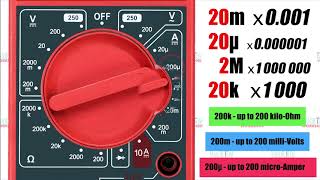
How to use a Multimeter? The ULTIMATE Guide you've been looking for!
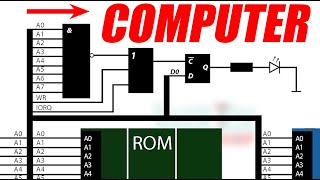
How do computers work? CPU, ROM, RAM, address bus, data bus, control bus, address decoding.

All Electronic Components Explained In a SINGLE VIDEO.

Mastering SOLDERING. TOP 10 mistakes YOU make as a beginner!

How to power any LED and NOT turn it to smoke?

Can a virus set your PC on FIRE?

SEVEN hidden WINDOWS features that YOU are NOT AWARE of!

7 MOST Notable Hackers of All time. Kevin Mitnick, Albert Gonzalez, Gary McKinnon, Julian Assange.

Windows Command Prompt Secrets YOU did NOT know!

Is your phone being TAPPED? Find out NOW - in 3 simple steps!

What is a Bruteforce attack? Youtube Workshop.

ENCRYPTION -- How does it work? Explained in VERY simple terms.

THIS IS HOW Messenger App in YOUR phone can be easily HACKED. Man-In-The-Middle Attack EXPLAINED.

Trojans, AutoRun, USB Jackers, DDoS, Worms, Keyloggers, Botnets, Cryptojackers, Ransomware EXPLAINED

The famous "Wear Sunscreen" Commencement Speech. What's really behind it?

How to spot a PROFESSIONAL TROLL? Tweaking social media algorithms to manipulate users biases.

How to keep your CRYPTO safe? Hackers in search of a secret formula.