Petronella Devi

4.2.2: Velocity Estimates - Agile Planning for Software Products

Software Architecture in the Development Process - Software Architecture for the Internet of Things

Software Architecture: Definition - Software Development Processes and Methodologies

Is anyone wiser than Socrates? - Know Thyself - The Value and Limits of Self-Knowledge: The

Export Finance - Global Financing Solutions (by EDHEC and Société Générale)

The REPL and Errors - Programming Languages, Part A

Variable Number of Function Arguments - Introduction to Programming with MATLAB

Sprite Class - An Introduction to Interactive Programming in Python (Part 2)

Finding Bugs in Code - Programming Foundations with JavaScript, HTML and CSS

2.2 Futures in Java's Fork/Join Framework - Parallel Programming in Java

6.2 Sexual process and life cycles - Protists: Evolution and Ecology of Microbial Eukaryotes

4.7 STL Example - C++ For C Programmers, Part A
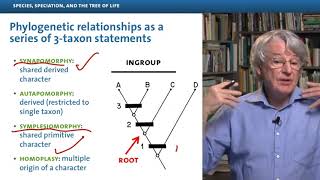
Species, Speciation, and the Tree of Life: Part 2 - Evolution: A Course for Educators

6.3 Phylogenetic tree of eukaryotes - Protists: Evolution and Ecology of Microbial Eukaryotes

Rate of Neutral Molecular Evolution (S) - Introduction to Genetics and Evolution

SAS Lesson 3 - Measures of center and spread - Data Management and Visualization

Tools and Sites for Plain Language - Foundational Skills for Communicating About Health

CERC and How Communicating During a Crisis Is Different - Communicating During Global Emergencies

Community-Based Implementation of CDC PrEP Guidelines - PrEParing: PrEP for Providers and Patients

Epidemic Characteristics and Response Strategies - Lecture Series for Preventing and Controlling

Intro to the Cash Flow Statement - Financial Analysis Tutorial

Installing Elixir - Elixir Tutorial

How to initiate a project - Project Management Tutorial

4 steps of delegation - Leadership Tutorial

Dev Environment Overview in Hibernate - Spring Framework Tutorial

Bean Scopes - Overview - Spring Framework Tutorial

Network Discovery with Scapy - Kali Linux Tutorial

Exploitation with Metasploit Pro - Kali Linux Tutorial

Introduction to Variational Autoencoders - Generative Adversarial Networks (GAN) Tutorial

Ensemble Learning - Bagging and Bossting - R Tutorial