Blue Turtle Technologies
Blue Turtle provides solutions that allow customers to greatly improve the adoption of agile development, provide security for data, databases and applications, and enable delivery of digital services. We work with innovative technology vendors, tailoring solutions to drive business value, delivered by a multi-disciplined team working in partnership with our customers.

Software Asset Management as a Service (SAMaaS)

Ivanti Security Controls: Patch Management Deep Dive

Ivanti Security Console Overview with Blue Turtle

BMC Control-M South African Automation Webinar

How to ensure maximum availability and performance for your Office 365 applications.

Why it’s time to rethink your approach to SAP Monitoring.

Blue Turtle and Redgate DATABASE DEVOPS IN A DAY

Get to the root of your Digital Workspace performance problems

Disrupt the Status Quo

Cynet 360 AutoXDR™ Cybersecurity Platform – 11 minute Demo

One Identity | Quest: A market leader in unified identity security

BitSight: Bringing Universal Understanding to Cyber Risk

StrikeReady - A Human First Approach

Finding Apache Log4J Vulnerabilities in your Attack Surface
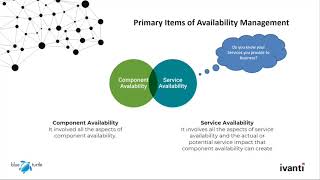
Blue Turtle and Ivanti | Service Modelling and Availability Management

Enabling the Autonomous Digital Enterprise with BMC Digital Business Automation

Enabling the Autonomous Digital Enterprise

Control-M - Automation of application workflow orchestration within Retail enterprises

Blue Turtle & Ivanti Virtual Event Autonomous Endpoint and Discovery Management

Blue Turtle / Ivanti Update

Control M User Group Forum - Big Data

Reinventing Customer Service with End-to-End AI-Driven Hyperautomation

Achieving new levels of accuracy with IDP

Alsid webinar Teaser

Blue Turtle On Demand Webinars Now Available

A New Way to Isolate Your Workspace - Blue Turtle and Hysolate

How to Build a Secure and Compliant Cloud Landing Zone with Blue Turtle and Trend Micro

IAM not securing Active Directory! It's more complex than it SIEMS | Blue Turtle and Alsid Webinar

Leveraging Change Control to Improve attack resistance

Leveraging Change Control to Improve attack resistance