Naj Qazi
As a seasoned tech expert in Silicon Valley with over 20 years of experience as a Computer Engineer and more than a decade as an IT Instructor, I’ve launched this channel to share my knowledge and guide you towards achieving your educational and career aspirations. Let's embark on this journey together and unlock your full potential! 💪
Areas I cover on this channel:
📚 Certifications: CCNA, CCNP & More!
👨💻 Network Engineering & Sales Engineering!
🚀 IT Career Development & Industry Insights!
If you follow this channel, I guarantee that you will find super valuable content that will turn you into a productivity monster and take your career to the next level. So what's holding you back? Hit subscribe and let's go 🚀

Ansible, Chef, Puppet Explained: Master Network Configuration Management Tools in Minutes!
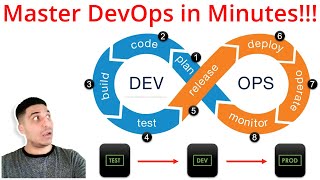
Master DevOps Concepts in Minutes!

JSON Simplified: Crack the Code on Network Automation - Part 2

JSON Simplified: Crack the Code on Network Automation - Part 1

Master HTTP Verbs & URI in 6 Minutes

Public Cloud & IaaS Explained in 4 Minutes!

Server Wars: Tower vs. Rack vs. Blade - What’s Best for You?

From AI Ready Data Center to Private Cloud IaaS: Step-by-Step Guide

From Physical to Virtual: The Complete Guide to Server Virtualization Fundamentals

Cisco SDA vs Traditional Access Layer: The Game-Changer You've Been Waiting For

AI-Powered Networking: From Zero to SDA Hero in 11 Minutes!

Cisco ACI Explained: Master Spine-Leaf Architecture in Minutes!

3 Reasons for the Rise of SDN

Centralized vs Distributed Control Plane

REST API: HTTP Verbs | POST, GET, PUT, DELETE

What is an API? | Northbound & Southbound APIs Explained

Why so many SDN Solutions? ACI vs DNAC vs Viptela

What is IPS? | Traditional IPS vs Next-Gen IPS

Difference between Firewall and Next Generation Firewall

What is a Firewall: Why do you need it?

What is DHCP Snooping and Dynamic ARP Inspection?

What is Port Security and How to Configure it?

What is AAA Security?

Cyber Security Defense Techniques (Part 2)

Cyber Security Defense Techniques (Part 1)

Most Common Security Threats (Part 3)

Most Common Security Threats (Part 2)

Most Common Security Threats (Part 1)

Overview of Network Security

Wildcard Masks: What Are They And How Do They Work?