Cyber Security 2024

Introduction to Cyber Crimes and Cyber Laws

Present and Future of Artificial Intelligence #Future #artificialintelligence #ksrce #cybersecurity

Intellectual Property Rights in Cyber Crimes and Laws #cybersecurity #Crimes #law #ksrce

Variables in C Programming | Easy Explanation for Beginners! #ksrce #cybersecurity #variables #c

Cloud service models #Cloud #service #models #ksrce

Cloud deployment models #cloud #cybersecurity #ksrce #model

Basic Operational Concepts in Computer Organization and Architecture #coa #cybersecurity #ksrce

CPU Scheduling Algorithm – SJF, #cpu #cybersecurity #SJF #ksrce

CPU Scheduling Algorithm – FCFS #ksrce #cpu #schdule #algorithms #cybersecurity

Singly Linked List in Data Structure #cybersecurity #datastructures #singlylinkedlist

Introduction to Data Structures and Algorithms #Data #Structures #Algorithms #KSRCE #cybersecurity

Types of Intelligent Agents in AI #cybersecurity #ai #Intelligent #agent

#HTTP request and HTTP response using #servlet. #KSRCE #cybersecurity

How to execute a #Servlet program step by step? KSRCE, #Cybersecurity

#Document #Object #Model KSRCE in #Web #Technology

#Servlet #Life #Cycle #KSRCE #cybersecurity

#Constructor #Overloading #Method #Overloading in #Java #programming #KSRCE #cybersecurity

K S R #College of #Engineering #Programming in #Java

Programming in Java - Class and Object

Concept of SQL Injection

Find the XSS vulnerability in the web application
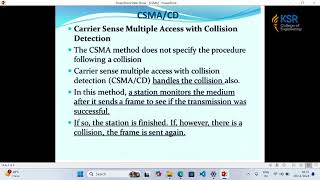
Carrier Sense Multiple Access (CSMA)

Cloud computing Architecture

Concept of Computer Architecture and Organization

Queue In Data Structure

Computer Network

Ethical Hacking

Java Program

Vinayagar Songs