Arthur Salmon
Hello and welcome,
I am an instructor that teaches a lot of Cybersecurity, Networking, and programming courses. Often these videos are embedded in my course shells, but I make most of them available for everyone. I do make custom content for those I am working with. If you are needing certain help reach out. Keep in mind this is not my full-time job so it may take a few days for a response, but I try to get all messages answered.
If you want to contact me
Email: [email protected]

CCNA1-ITNv7 - 17.5.9 Packet Tracer - Interpret show Command Output

JBL — Безопасность Интернета и веб-приложений — ГЛАВА 12 — Тестирование и обеспечение качества ве...

JBL — Безопасность Интернета и веб-приложений — ГЛАВА 08 Разработка безопасного Интернета и веб-п...

CCNA1-ITNv7 — 16.5.1 Packet Tracer — безопасные сетевые устройства

JBL — Безопасность Интернета и веб-приложений — ГЛАВА 09 — Устранение уязвимостей веб-приложений

CCNA1-ITNv7 - 13.2.6 Packet Tracer - Проверка адресации IPv4 и IPv6

CCNA1-ITNv7 — 13.2.7 Packet Tracer — использование Ping и Traceroute для проверки сетевого подклю...

CCNA1-ITNv7 — 13.3.1 Packet Tracer — использование ICMP для тестирования и исправления сетевого п...

JBL — Безопасность Интернета и веб-приложений — Глава 10 — Оценка уязвимости веб-сайта

JBL - Internet and Web Application Security -- Chapter 06 - Web Application Security

JBL - Internet and Web Application Security -- Chapter 05 - Mitigating Website Risks, Threats, &Vuln

JBL - Internet and Web Application Security -- Chapter 01

JBL - Internet and Web Application Security -- Chapter 04

CCNA1-ITNv7 - 16.4.6 Packet Tracer - Configure Secure Passwords and SSH

CCNA1-ITNv7 - 14.8.1 Packet Tracer - TCP and UDP Communications

CompTIA Sy0-701 Security+ - Review Questions 001

CCNA1-ITNv7 - 11.7.5 Packet Tracer - Subnetting Scenario

CCNA1-ITNv7 - 11.5.5 Packet Tracer - Subnet an IPv4 Network

CompTIA - Security+ - (SY0-701) Chapter 06 - Understanding Common Threat Vectors and Attack Surfaces

CompTIA - Security+ - (SY0-701) Chapter 05 - Compare and Contrast Common Threat Actor and Motivation

CompTIA - Security+ - (SY0-701) Chapter 04 - Understanding the Importance of Using

CompTIA - Security+ - (SY0-701) Chapter 03 - Understanding Change Management’s

JBL - Managing Risk in Information Systems - - CHAPTER 13 - Mitigating Risk with a BCP

JBL - Managing Risk in Information Systems - CHAPTER 12 - Mitigating Risk with a BIA

CCNA1-ITNv7 - 12.9.1 Packet Tracer - Implement a Subnetted IPv6 Addressing Scheme

CCNA1-ITNv7 - 12.6.6 Packet Tracer - Configure IPv6 Addressing

CCNA1-ITNv7 - 10.3.4 Packet Tracer - Connect a Router to a LAN

CCNA1-ITNv7 - 10.3.5 Packet Tracer - Troubleshoot Default Gateway Issues

JBL - Managing Risk in Information Systems - CHAPTER 11 - Turning a RA into a Risk Mitigation Plan
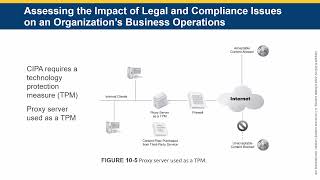
JBL - Managing Risk in Information Systems - CHAPTER 10 - Planning Risk Mitigation Throughout an Org