Insekube - TryHackMe - Kubernetes - Grafana Platform Local File Inclusion
Автор: Security_cnr
Загружено: 2022-09-12
Просмотров: 628
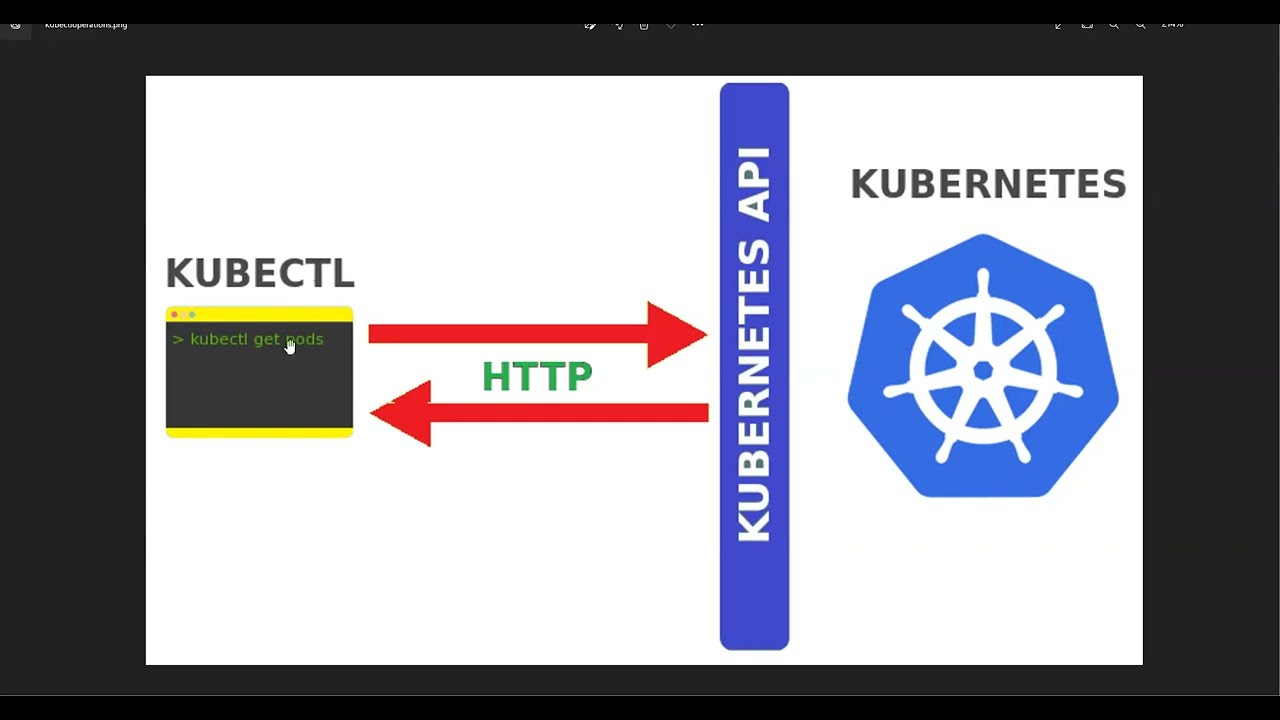
This lab demonstrates how one of the pods in the Kubernetes environment can be hijacked by leveraging a Grafana Local File Injection vulnerability. It is demonstrated that bad actors were able to navigate outside the Grafana folder and remotely access restricted locations on the server. In this tutorial, we reached to the token of the service account running a pod. To achieve pod privilege escalation, an "Everything Allowed" type pod was created. Using the exec command in the pod, a shell session was established with root privileges.
Доступные форматы для скачивания:
Скачать видео mp4
-
Информация по загрузке:



















