Remote Code Execution (RCE) Vulnerability Bug Hunting
Автор: Rahad Chowdhury
Загружено: 10 февр. 2023 г.
Просмотров: 11 514 просмотров
Remote Code Execution (RCE) Vulnerability Bug Hunting | Rahad Chowdhury
Remote code execution (RCE) refers to a class of cyberattacks in which attackers remotely execute commands to place malware or other malicious code on your computer or network. In an RCE attack, there is no need for user input from you.
RCE vulnerabilities are almost always considered critical, and finding and patching them should be among your top priorities. Network security has come a long way from the worms of the 1980s, and RCE attacks can be remarkably complex and difficult to spot. What does an RCE attack look like in the 21st century, and what can you do to protect your company?
If You face any Problem You can Contact with Me
..............................................................................................................
Contact:::
..............................................................................................................
Facebook:
/ rahadchowdhury
..............................................................................................................
Web: https://rahadchowdhury.info
Read Blog:
...............................................................................................................
Linkedin:
/ rahadchowdhury
..............................................................................................................
Twitter: / hinad5
..............................................................................................................
#RCE
#RemoteCodeExecution
#RemoteCommandExecution
#RCEVulnerability
#RCEBug
RCE
Remote Code Execution
Remote Code RCE
Remote Code Execution - RCE
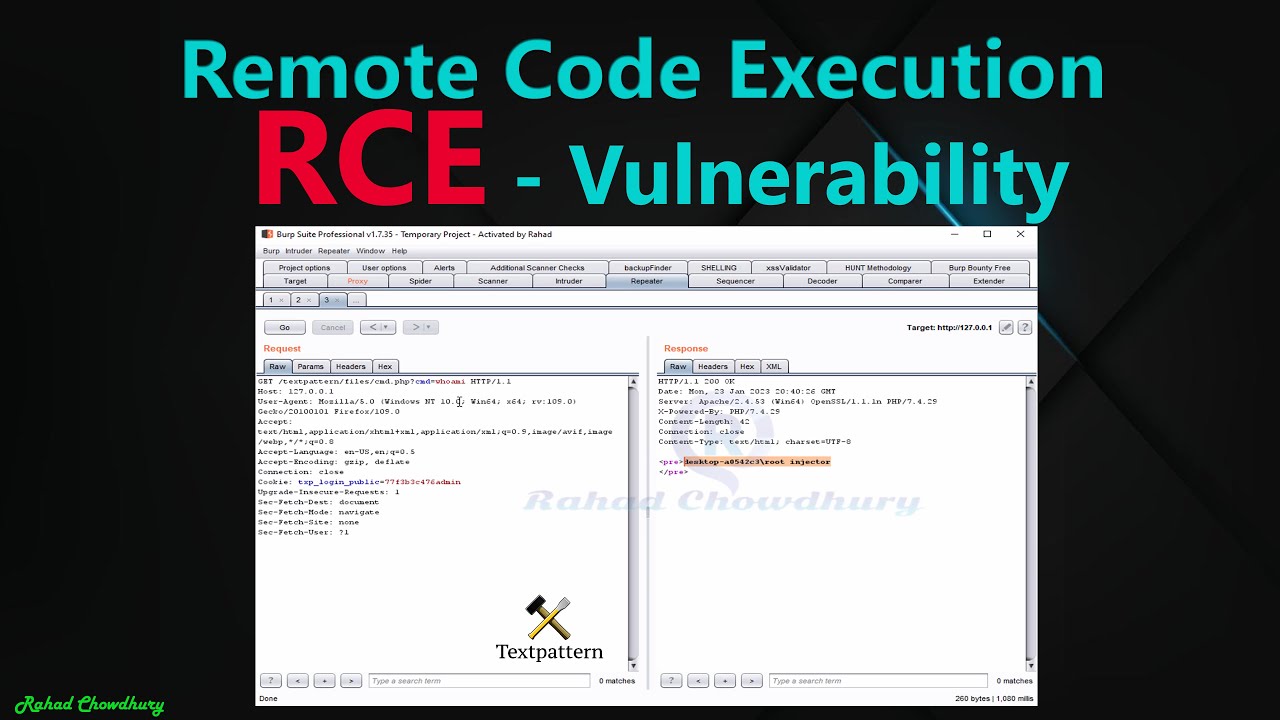
TextPattern CMS RCE
Remote Command Execution
Remote Command Execution (Authenticated)
TextPattern - Remote Command Execution
Remote Command Execution POC
RCE POC
TextPattern CMS
TextPattern
TextPattern CMS 4.8.7
TextPattern CMS 4.8.8
TextPattern CMS 4.8.9
TextPattern CMS Remote Code Execution
TextPattern CMS Remote Command Execution
RCE Proof Of Concept
RCE Authenticated POC
TextPattern RCE
TextPattern Remote Command Execution
Remote Command Execution
TextPattern CMS
TextPattern
remote control execution
remote code execution vulnerability
remote code execution via web shell upload
remote code execution tutorial
remote code execution poc
remote code execution (rce)
remote code execution bug bounty
remote code execution bug bounty
remote code execution explained
remote code execution in hindi
remote command execution
remote command injection
RCE vulnerabilities
remote command execution attack
Remote Command Execution(RCE)
Vulnerability PoC
Remote Command Execution Explained and Demonstrated
Arbitrary code execution
rce
rce vulnerability
arbitrary code execution remote code execution
remote code execution poc
rce
rce attack
remote code execution (rce)
xs info
rce vulnerability poc
rce poc video
rce tutorials
xs infosol
remote command execution youtube
rce videos
rce hackerone
rce hackerone reports
exploiting rce
Доступные форматы для скачивания:
Скачать видео mp4
-
Информация по загрузке: