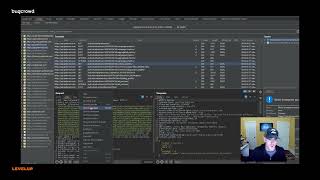
Critical IDOR Leading to Full Account Takeover | $2,500 Bug Bounty PoC on SuryaElectronics.in
Автор: WhiteHat Workspace
Загружено: 2025-07-24
Просмотров: 3991
In this video, I demonstrate a Critical IDOR (Insecure Direct Object Reference) vulnerability I discovered on SuryaElectronics.in that led to full account takeover — without needing user interaction or credentials. This vulnerability allowed unauthorized access to any user’s personal data, including order history, addresses, and even the ability to modify account settings.
🛡️ This issue was responsibly disclosed and rewarded with a $2,500 bug bounty under their private bug bounty program.
WhatsApp Group: https://whatsapp.com/channel/0029Vb6R...
🔍 Watch the step-by-step PoC (Proof of Concept) where I:
Identify the vulnerable API endpoint.
Bypass access control using simple ID manipulation.
Take over a user account without authentication.
Explain the root cause and potential impact (CVSS 9.8+).
Share remediation advice for developers
⚠️ For educational purposes only. Do not attempt this on systems you don’t own or have permission to test.
🧠 Topics Covered
IDOR vulnerability explained
Real-world bug bounty hunting
Account takeover via broken access control
API security testing using Burp Suite
Ethical hacking in action
📢 Don’t forget to like, share, and subscribe for more real-world bug bounty case studies and hacking tutorials!
how to find idor, critical web vulnerability, idor bug bounty, security researcher, ethical hacker 2025, bug bounty india, idor explained, broken authentication, api security flaws, hacking indian websites, burp suite idor, cyber security tips, responsible disclosure program, web hacking 2025, hackerone tips, bug bounty hunting, idor bug explained, access control bypass, api endpoint vulnerability, real bug bounty example, hacking step by step, web app exploit, critical auth bug, session management flaw, exploit development, security bug report, find critical bugs, idor vulnerability tutorial, bug bounty learning

Доступные форматы для скачивания:
Скачать видео mp4
-
Информация по загрузке: