dns tools lab demonstration -normal vs malicious output (dig, nslookup, host, dnsrecon, dnsenum)
Автор: it-bs media
Загружено: 2025-12-14
Просмотров: 61
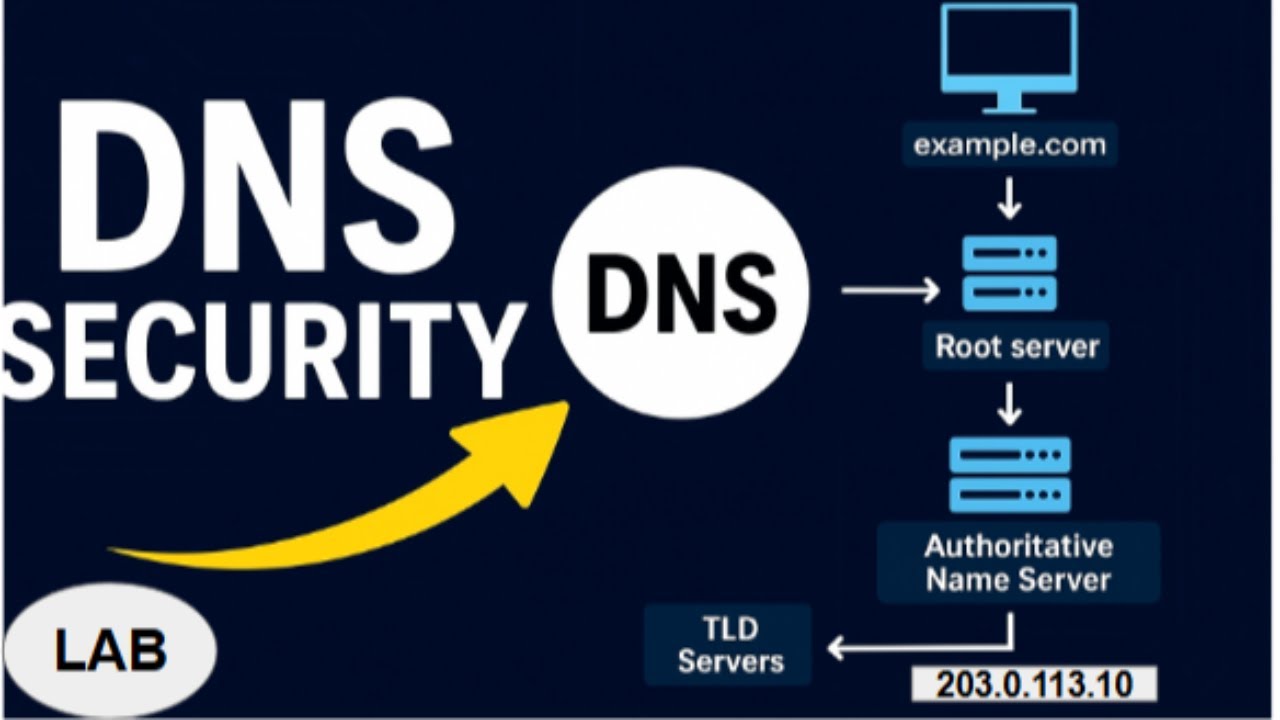
DNS is one of the most trusted—and most abused—protocols on the internet. In this tutorial, you’ll learn how to read DNS tool output like a SOC analyst by comparing normal DNS behavior vs malicious activity using real command-line tools.
We break down the outputs of dig, nslookup, host, dnsrecon, and dnsenum, showing you exactly how attackers hide command-and-control traffic, abuse DNS misconfigurations, and how defenders detect it.
This is not just how to run tools — it’s how to think like a cybersecurity professional.
Доступные форматы для скачивания:
Скачать видео mp4
-
Информация по загрузке:



















