Zeek in Action, Video 1, Suspected Malware Compromise
Автор: Zeek
Загружено: 2021-04-14
Просмотров: 25119
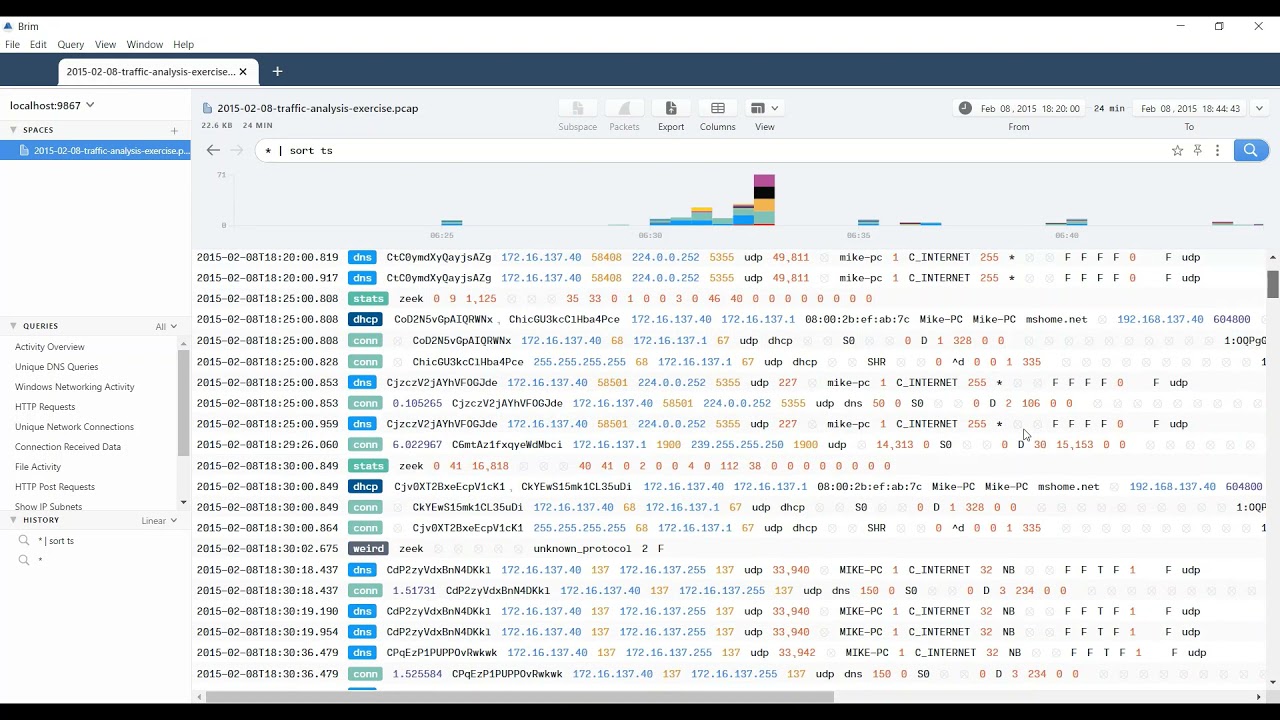
The first video examining network traffic using Zeek and related applications is now available. This episode looks at a suspected malware compromise, posted by Brad Duncan on his Malware Traffic Analysis site. We use Brim to create Zeek and Suricata logs from a packet capture, and then we review the outputs for signs of suspicious and malicious activity.
Доступные форматы для скачивания:
Скачать видео mp4
-
Информация по загрузке:



















