IEEE 802.1X | Understanding 802.1X Authentication | What is IEEE 802.1X and How does 802.1X work?
Автор: Rajneesh Gupta
Загружено: 9 мая 2022 г.
Просмотров: 24 554 просмотра
✔ ✔ ✔ In This lesson you will learn - Introduction about What is IEEE 802.1X and How does 802.1X work?
IEEE 802.1X | Understanding 802.1X Authentication | What is IEEE 802.1X and How does 802.1X work? by Rajneesh Gupta
--------------------------------------------------------------------------------------------------------------------------------------------------
[FREE GUIDE] 7 Steps to get Cybersecurity Job in 90 days go.haxsecurity.com/7-steps-cybersecurity-jobs-in-90days
👉🏻 Ultimate SOC Analyst Course learn.haxsecurity.com/services/security-analyst
----------------------------------------------------------------------------------------------------------------------------------------------------
✔ 802.1X | Network Basics
✔ Understanding 802.1X and NAC
✔ What is the security benefit of using 802.1x wireless protocol?
✔ What Is 802.1X? How Does It Work?
✔ How to Configure IEEE 802.1X Port Based Authentication
✔ Standard IEEE 802.1X - macmon Partner - ITB
✔ Wie funktioniert IEEE 802.1x
✔ How does IEEE 802.1X work?
✔ What is IEEE 802.1X infrastructure?
✔ What does IEEE 802.1 stand for?
✔ Is IEEE 802.1X wireless?
✔ What is an example of an IEEE standard?
✔ What does IEEE 802.1 Q concern?
✔ Which one of the IEEE 802 committees is tasked with the development of security standards?
✔ What is QinQ in networking?
✔ How many IEEE standards are there?
✔ How does Wi-Fi authentication work?
✔ What is Wi-Fi NAC?
✔ What is IEEE authentication?
✔ What is IEEE 802.1Q quizlet?
✔ What is a trunked VLAN?
✔ What is 802.1Q used for?
✔ Are IEEE standards Law?
✔ How are IEEE standards developed?
✔ What type of standard making body is IEEE?
----------------------------------------------------------------------------------------------------------------------
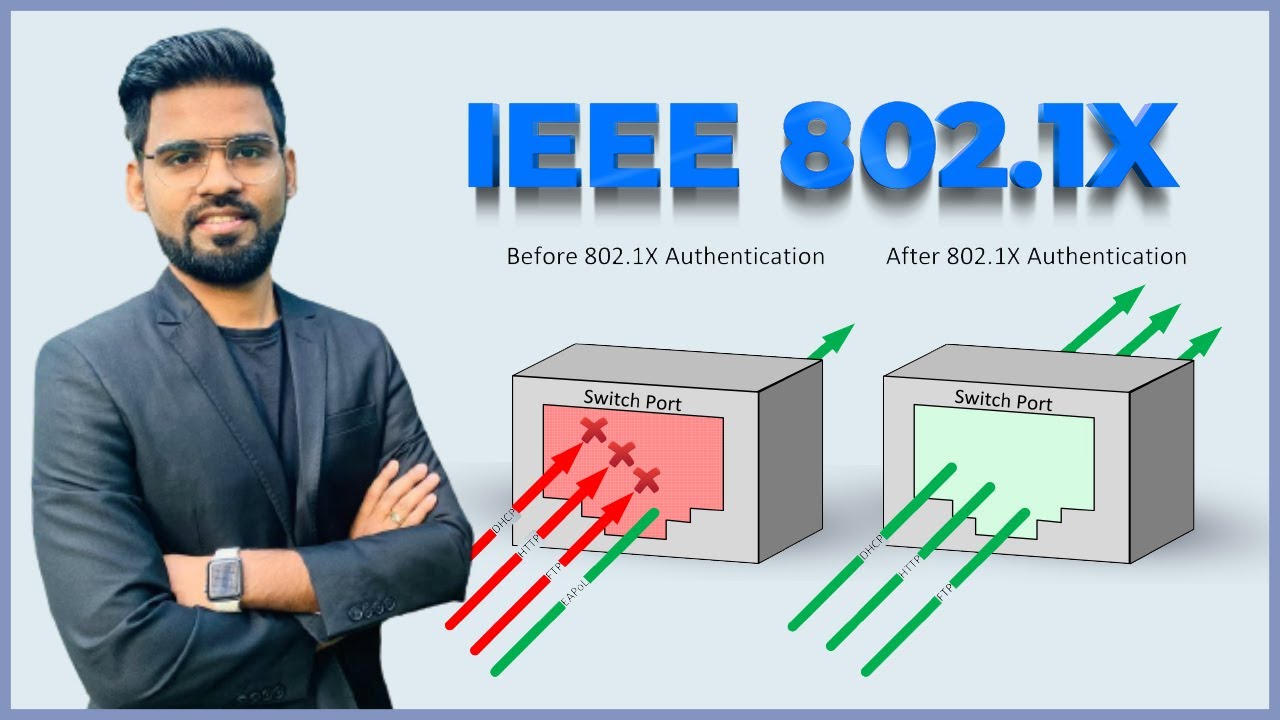
Ques: What is IEEE 802.1X?
Devices attempting to connect to a LAN or WLAN require an authentication mechanism. IEEE 802.1X, the IEEE standard for port-based network access control (PNAC), provides protected authentication for secure network access.
An 802.1X network differs from a home network in one major way; It has an authentication server called RADIUS server. It checks the user's credentials to see if they are an active member of the organization and, depending on network policies, grants users different levels of access to the network. This allows the use of unique credentials or certificates per user, eliminating the reliance on a single network password that can be easily stolen.
How does 802.1X work?
802.1X is a network authentication protocol that opens ports for network access when an organization authenticates a user's identity and authorizes them to access the network. The identity of the user is determined based on their credentials or certificate, which is verified by the RADIUS server. The RADIUS server is able to do this by communicating with the organization's directory, typically over the LDAP or SAML protocol.
-----------------------------------------------------------------------------------------------------------
Want to kickstart your Cybersecurity career? or want some pro tips on ethical hacking or cybersecurity tools, techniques, and competition program? you can
SIGN UP HERE: https://learnwithrajneesh.com/
Please don’t forget to Like, Share & Subscribe
☑ Watched the video!
☑ Liked?
☑ Subscribed?
--------------------------------------
☑ YouTube -- / rajneeshcyber
☑ Twitter -- / rajneeshcyber
--------------------------------------
#IEEE_802.1X #comptia+ #rajneesh_gupta #Authentication #ethical_hacking #Rajneesh #cybersecurityforbeginners #cybersecuritycareers
Доступные форматы для скачивания:
Скачать видео mp4
-
Информация по загрузке:








![How are Images Compressed? [46MB ↘↘ 4.07MB] JPEG In Depth](https://ricktube.ru/thumbnail/Kv1Hiv3ox8I/mqdefault.jpg)
